How Targeted Phishing Became a Massive Cybersecurity Threat and How to Protect Your Practice
If a major technology company like Cloudflare can get attacked, so can your small clinic.
In July 2022, the
Cloudflare Security department got alerts about employees getting seemingly legitimate texts pointing them to a fake Cloudflare Okta login page.
Their records indicate that the targeted SMS phishing attack began at 10:50 PM on July 20, 2022. Within a minute, 76 employees received these texts on their work phones, some even on their personal phones.
Here’s what the text messages employees received looked like:
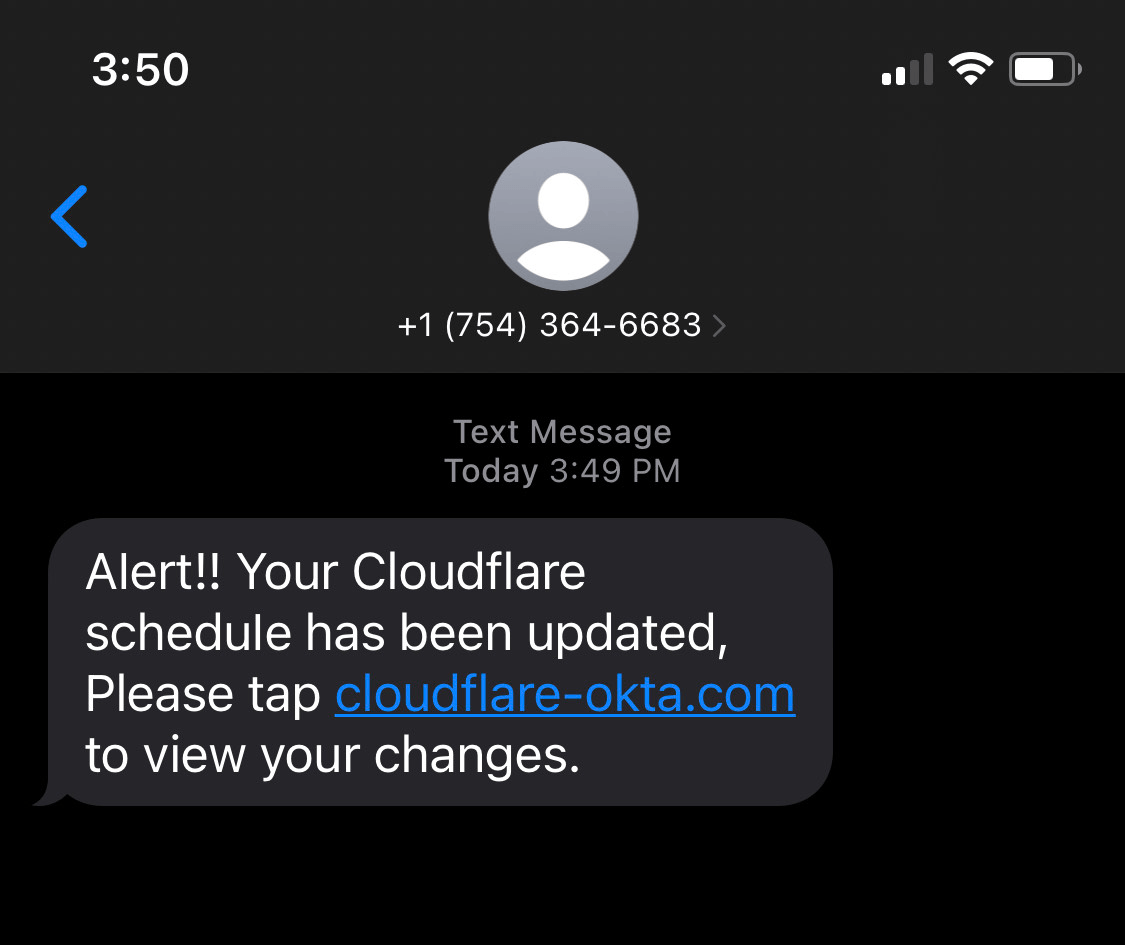
Photo from Cloudflare
What Is Phishing and Why Is It So Risky?
Phishing is a type of cyberattack where a scammer sends an email or text message to trick the recipient into clicking a link or opening an attachment, which can then infect their device with malware.
Phishing scams are becoming more common and more sophisticated. They are now able to target specific individuals or companies, and they may even be able to bypass spam filters.
Phishing messages appear to come from someone you know and trust, so it's important not to click any links in the messages. Medical practices are especially vulnerable to these types of scams because hackers know that personal health information (PHI) is valuable and can be used to exploit patients.
The Mechanics of Targeted Phishing Attacks
A targeted phishing attack is typically much more sophisticated than a regular phishing attack. The scammers gather information about their victims before they launch the attack. They often use social engineering and technical exploits to gain access to sensitive information. This makes it harder for victims to spot fake texts, emails, or websites.
The goal of a targeted phishing attack is to obtain sensitive data from an organization or individual with the intent of using it for illegal purposes such as identity theft and financial fraud.
The following are some of the things that you should be aware of when it comes to phishing scams in the workplace:
- Phishers will often send out emails with attachments that contain malware or links that lead to a phishing site.
- Phishers will often use subject lines that involve the email address of someone in the company as well as companies in general so that they can lure people into opening emails.
- Phishers will often use words like urgent, emergency, and critical in order to get people’s attention and convince them into opening the email or clicking a link.
- Phishers will often use official-looking company logos as well as fake sender addresses so that they can trick people into opening an email that is telling them to click a link or to download an attachment.
- Phishers may ask for personal information such as passwords, account numbers, social security numbers, and bank accounts.
How to Prevent Targeted Phishing Attacks
There are some best practices that can help your medical organization prevent these types of attacks. Make sure all your clinic staff follows these procedures:
Keep Hardware and Software up to Date
Scammers can exploit security vulnerabilities in outdated software. Make sure all of your devices are running the latest version of their operating system and that all security patches are installed.
By keeping your software updated, you’ll make it more difficult for attackers to get into your systems.
Proactive IT support for healthcare practices does this regularly and promptly.
Have Strong and Unique Passwords
With multiple accounts needing passwords, it's much easier to come up with something simple and memorable and reuse it across all platforms. When an attacker gains access to one, they've pretty much gained access to everything else.
To prevent these types of attacks, you must have strong and unique passwords for all your accounts, not just for your work account but for any account that you have.
A password with eight characters is recommended in most environments. In healthcare, it's wise to
use a password with 11 characters.
To help you create strong and unique passwords for each account, you can use password managers like LastPass or 1Password. They can generate and store complex passwords for you so you don't have to worry about remembering them.
Enable Two-Step Verification
You can prevent targeted phishing attacks by enabling two-step verification on your email and social media accounts.
Two-step verification is a security measure that requires a user to provide two pieces of information to verify their identity. This means that the user needs to have access to their phone and input a code that is sent by SMS or generated by an app. The code can be used for logging into an account or accessing sensitive data.
This type of authentication makes it very hard for hackers to get access to your account because they need both your password and the extra authentication code. Two-step verification is especially important when using public Wi-Fi networks, as these are more vulnerable to hacking attempts than private networks.
Anytime you get a verification code even if you never attempted to log in, you should change your password right away.
Don’t Click Links in Email or Text Messages
Most people are aware that they shouldn’t click links in email messages from strangers, but many don’t know that they should also be careful about clicking links in text messages.
Text message phishing, also known as smishing, is a type of targeted phishing attack. Attackers send text messages that appear to be from a legitimate source, such as a bank or popular online retailer. The message usually includes a link that takes the victim to a fake website designed to steal their personal information.
Smishing attacks are on the rise because they are difficult to detect and can be very convincing. If you receive a text message with a link, do not click it. If you’re not sure if the message is legitimate, contact the company directly using a phone number or website you know is real.
Don’t Give Out Personal Information on Social Media
As we become more accustomed to social media, it's easy to forget that not everything should be shared online. Hackers can use this information to target you in phishing attacks.
Social media isn't a place to put personal information. These details can be cataloged and sold by hackers to the highest bidders. In 2021, for instance, a certain Tom Liner scraped 700 million LinkedIn records.
These attacks are becoming more and more common, and they can be difficult to spot. That’s why it’s important to be careful about what you share on social media. Don’t post your full name, address, or phone number on any public platform.
Be aware of the privacy settings for each site you use, and only share information with people you know and trust. If you do receive a suspicious message, don’t reply or click any links.
Use a Security Solution That Has Anti-phishing Protection
Security solutions are a must for any establishment. Besides protecting a company from cyber threats, they also make sure it doesn't lose its reputation.
Ideally, a reliable security solution includes anti-phishing protection. It’s important to have a system that can detect phishing attacks and protect against them. This is because there are many people who fall for phishing attacks–even those who are aware of the dangers!
Anti-phishing protection is a type of security solution that includes various tools that can detect phishing emails and prevent them from being delivered to your inbox. There are also anti-phishing cloud services that allow you to detect, analyze, and prevent potential phishing attacks.
Stay updated on the latest phishing scams
One of the most effective ways to protect against these attacks is by staying informed about the latest phishing scams. Not only will you be able to recognize a scam when you see it, but you will also have an idea of what information would be valuable for them to steal from your organization.
The security team at your organization should update their employees on new threats regularly. This will help ensure that they know how to identify and avoid them in the future.
Educate your employees
Your employees are the first line of defense against targeted phishing attacks. You should educate them about how to spot phishing attacks.
Teach them to be suspicious of unsolicited emails, even if they seem to come from a trusted source. If an email or text looks suspicious, they should not click any links or open any attachments.
With healthcare being so lucrative, rigorous cybersecurity awareness training paired with
simulated phishing campaigns are more critical than ever. This brings us to the next section.
How Cybersecurity Training and Phishing Simulation Boosts Your Protection
When it comes to cybersecurity, there is no one-size-fits-all solution. However, providing employees with cybersecurity training and phishing simulations is a great way to boost your organization's protection.
Cybersecurity training can help employees understand how to identify and avoid phishing attacks, and phishing simulations can provide a real-world test of those skills.
If you regularly test your employees with phishing simulations, you can identify potential vulnerabilities and take steps to mitigate them.
By combining these two tools, you can create a strong defense against phishing attacks and other cyber threats.
Get Healthcare-Specific Cybersecurity Training and Phishing Simulations
Is your medical practice cyber secure? If not, depending on the type of damage and consequences, this can be extremely costly.
Many practices aren't prepared for a cyberattack or data breach. The reality of this situation is scary. Innocent lives could be lost, and a huge loss of income is inevitable. Even if only for a few weeks, who can operate without patient files?
Due to unnecessary time constraints and the associated costs of bringing in outside experts, most medical practices have failed to comprehend the need to maintain and manage their own cybersecurity team.
ER Tech Pros offers a healthcare cybersecurity training program that equips medical practitioners with the tools they need to defend against cyberattacks. We provide valuable training in the form of healthcare industry-specific phishing simulations and cybersecurity skill development, which will have an immediate impact on your practice's productivity, operations, and security culture.
Be one of our many satisfied clients who are now able to operate with confidence, knowing their practice is better protected against hackers.
Search Articles
Healthcare & Tech Articles

ER Tech Pros is a managed service provider (MSP) that specializes in catering to the IT needs of businesses across the globe. We have offices in Sacramento and the Greater Fresno area.
We use our cutting-edge technology, extensive experience, and global team of technology experts to ensure your IT network is in its most secure and optimal state.
We focus on your IT so you can focus on growing your company.
8795 Folsom Blvd, Ste 205
Sacramento, CA 95826
1501 Howard Rd, Ste 2
Madera, CA 93637
(855) ER-TECH-1 / (855) 378-3241
info@ertech.io
Resources
Search this Site
ERTech Pros | All Rights Reserved.












