There's mounting pressure on medical practices to improve patient outcomes and operate efficiently while reducing costs. Doing more with less, so to speak. This means sacrificing some things in favor of others.
As cybersecurity is not often considered one of the foremost concerns, not until a breach actually happens, it bears the brunt of budgetary constraints. Many medical practices settle for the traditional antivirus, with the misguided notion that "that covers it, that should be enough on the cybersecurity side."
Traditional antivirus, however, is no longer enough. It is not a catch-all solution: It works well in protecting against known threats, but it’s not designed to detect in real time never-before-seen malware.
Cyber threats are evolving constantly. Thankfully, an evolution in cybersecurity is able to keep up. This is called
endpoint detection and response, or
EDR.
What Is EDR and How Does It Work?
Endpoint detection and response (EDR) is a new approach to cybersecurity, one that combines the detection of malicious behavior through historical data and analytics with the ability to respond quickly.
EDR solutions are designed to detect malicious activity at the endpoint level—the end users’ devices such as laptops, mobile phones, desktop computers—before it can spread throughout your network. It does this by creating an environment where all endpoint activity is monitored continuously, providing a clear picture of what is happening on the user’s device. Real-time activities that involve applications, files, network traffic, and much more, are all collected in one place for analysis.
This makes EDR ideal for detecting advanced threats and zero-day attacks that have yet to be identified by security vendors.
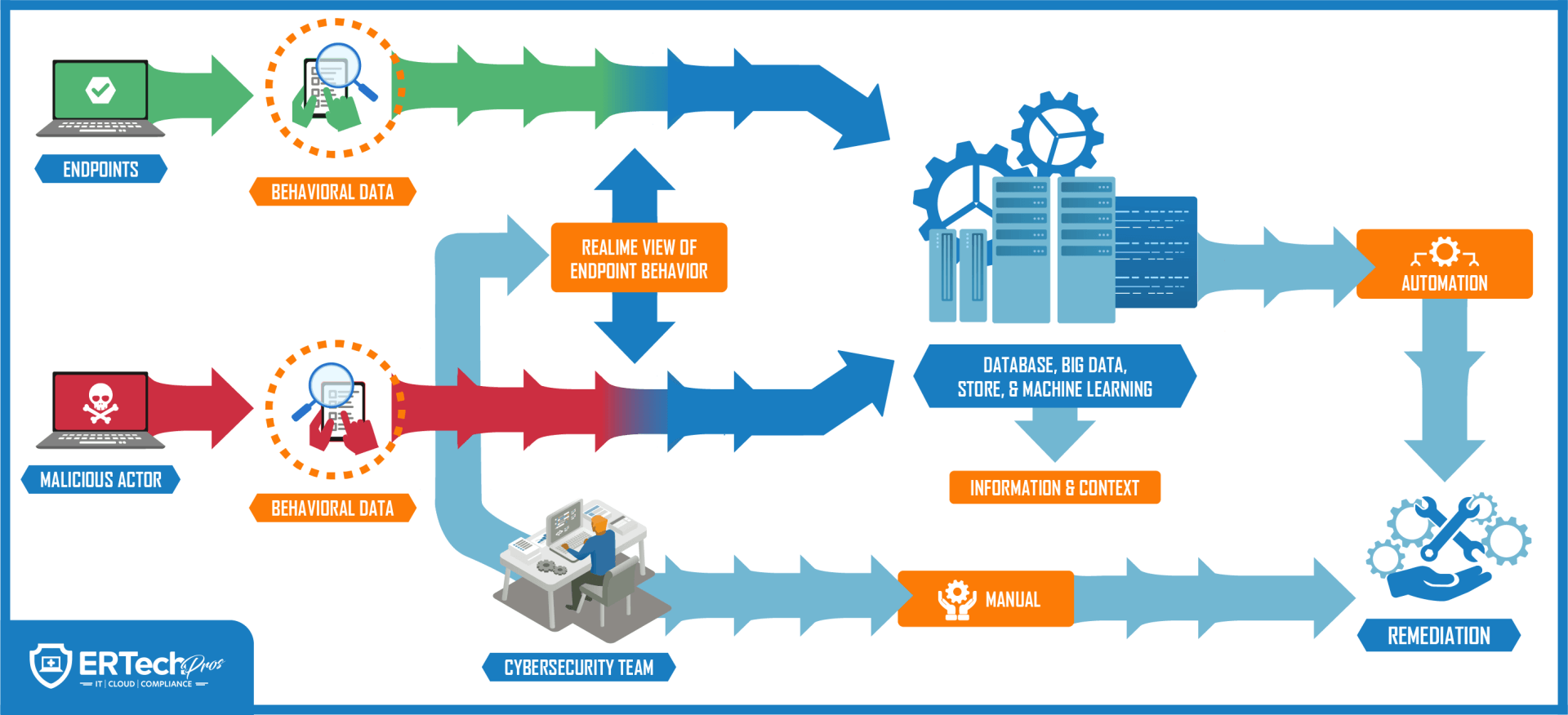
Here's an illustration of what happens behind the scenes:
Why Do Healthcare Practices Need EDR?
Healthcare data is highly valuable on the black market—and attackers know it. With so much personal information on file, it’s no wonder that hackers have been targeting healthcare companies for years in order to steal identities and hold data for ransom.
It’s estimated that
only four to seven percent of healthcare’s IT budget is spent on cybersecurity. Compared with other industries, such as the financial sector, cybersecurity budgets stand at
15 percent of their IT budget. This makes healthcare organizations an easy target for cyberattacks.
The time has come for them to reconsider their cybersecurity measures and invest in EDR solutions. Their purpose is to help organizations protect themselves against these attacks by quickly identifying an unauthorized change in the system, such as an infection, and responding with the right tools to fix it.
Essentially, EDR gives healthcare organizations an added layer of protection against cyberattacks.
Key Features of EDR That Benefit Medical Clinics
EDR’s features extend far beyond the capabilities of the traditional antivirus. With EDR in place, your clinic will be better prepared to prevent cyberattacks from occurring in the first place.
Here's what EDR can do to protect your medical practice:
Automatic Detection of Stealthy Attackers
EDR is designed to detect what antivirus software can't see—including malware that uses advanced evasion techniques. By analyzing billions of events across all endpoints in real time, suspicious behavior is automatically detected. Threat actors will have their work cut out for them since any stealthy attempts at data breach will be instinctively uncovered.
Integration With Threat Intelligence
Reputable EDR providers have proprietary cyber threat intelligence integration to make it much faster to identify malicious activities and tactics, techniques, and procedures (TTPs). A top example is ER Tech's
cybersecurity tech company of choice,
CrowdStrike.
Proactive Hunting, Investigation, and Advice on Threat Activity on Your Network
An optimal EDR system for medical practices includes having a security operations center (SOC) that is staffed 24/7 by security experts who provide alert, intelligent monitoring. Healthcare institutions need extra special attention when it comes to cybersecurity. This is why ER Tech Pros adds this feature on top of CrowdStrike's own threat hunters.
Visibility to Real-Time and Historical Data
When there's a comprehensive history of all activities on your network, trends and patterns are identified, providing insight into the attacker's strategy. This gives the security team the upper hand, when a sound plan of action can be developed to stop future attacks.
Accelerated Investigations and Remediation
The ideal EDR solution collects information from your endpoints and stores it in the cloud, growing a massive database of all activities with details and context. This way, SOC analysts have immediate access to historical and real-time data, making investigations go much more quickly, compounded by threat intelligence. When an endpoint is seen to have been compromised, it will go under containment, isolated from all network activity to keep the rest of your infrastructure safe.
How to Choose an EDR Solution for Your Medical Practice?
Medical practices tend to settle for traditional antivirus protection, for fear that any advanced solution will cause a dent on their budget. Here's the thing: a good EDR solution requires the least amount of effort and investment yet still provides the highest level of protection.
How do you know if that's what you're getting from an EDR solution? Look for the following
6 key aspects of EDR and you're all set:
1. Endpoint Visibility
With the ability to see all of your endpoints in real time, threat activities are exposed and thwarted even as they attempt to breach your network.
2. Threat Database
With a variety of analytic techniques, EDR can mine massive amounts of data collected from endpoints for signs of attack.
3. Behavioral Protection
Effective EDRs require behavioral approaches that alert the security team of suspicious activities before a compromise occurs by searching for indicators of attack (IOAs).
Behavioral protection is a key component of an effective EDR. The product should cover all stages of the attack lifecycle, including reconnaissance, lateral movement, and exfiltration of data.
4. Insight and Intelligence
This is a very important feature of an EDR solution. Integration of threat intelligence provides critical insight into the attacker, including their motivations and intentions. This information can help prevent future breaches by identifying gaps in security controls.
5. Fast Response
With an EDR solution that provides fast response, you can prevent attacks from escalating into full-blown breaches. This is critical for organizations that have strict compliance and security requirements, such as the healthcare industry. This also allows your practice to resume operations right away.
6. Cloud-based Solution
An ideal EDR solution should be cloud-based. With this, cyber protection is centralized, and an endpoint's location doesn't matter, since it's protected wherever it is, even outside the office network. Search, analysis, and investigation are also done accurately and in real time.
Invest in Managed EDR with a Healthcare-Focused IT Provider
If you’re looking to invest in an EDR solution, it’s important to work with an experienced healthcare IT provider.
The company should have a strong track record of providing EDR solutions that help hospitals and other healthcare organizations reduce their risk of data breaches.
If this sounds like what you’re looking for, we can help. Our team of EDR experts will work with you to develop an appropriate solution that meets your needs and complies with HIPAA guidelines.
Schedule a no-obligation demo now to get a firsthand look at how our EDR software works.