Dangerous Misconceptions That Put Critical Infrastructures at Risk
On May 12, 2021, the White House issued an executive order to improve the nation’s cybersecurity and protect federal government networks—a move that it claims to be “the first of many ambitious steps the Administration is taking to modernize national cyber defenses.”
While this news sounds like something that concerns only the government, it actually emphasizes that cybersecurity requires more than government action.
Cybersecurity requires a partnership between the Federal Government and private sector.
The executive order encourages private sector companies like your practice to follow the Federal Government’s lead and take ambitious measures to augment and align cybersecurity investments with the goal of minimizing future incidents.
Why is this relevant?
All this is relevant simply because cyberattacks against critical infrastructures are on the rise. And these attacks affect you, your practice, and your patients.
The Cybersecurity and Infrastructure Security Agency (CISA) defines critical infrastructure as the physical and cyber systems and assets that are so vital to the United States that their incapacity or destruction would have a debilitating impact on our physical or economic security or public health or safety.
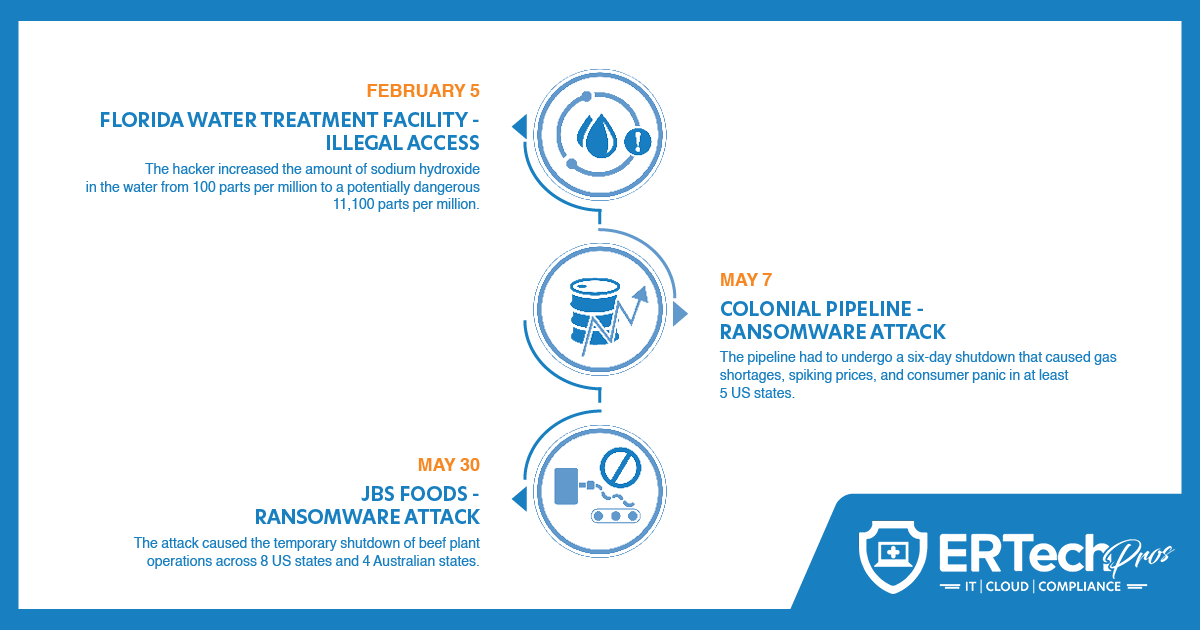
Here are a few recent attacks on critical infrastructures here in the US:
Critical infrastructures aren’t just power plants, transport systems, and military systems...they’re also food manufacturers, gas pipelines, and yes, the electronic healthcare systems you have in your practice.
You have critical infrastructure within your organization and you play a vital role in protecting it.
But where and how do you start?
Start by addressing misconceptions
The tech world is full of myths, misinformation, and misconceptions that can keep you from taking the first steps toward securing your critical infrastructure.
In a recent
webinar hosted by Cato Networks, CISA Cybersecurity Advisor Ron Ford explained how the US Federal Government, through CISA, is zeroing in on protecting critical infrastructure and how some misconceptions about cybersecurity can interfere with the process.
Here are some of the most common misconceptions that organizations like yours need to overcome:
I need a big budget!
Many organizations think being cyber secure means needing to have every single tool and technology. That’s not true.
It’s important to pace yourself. Ford calls this the crawl-walk-run approach.
Cybersecurity has a lot to do with the layered defenses of different solutions.
Identify the cybersecurity solutions that you already have (whether these are tools or training), fine-tune these solutions, and start drilling down on the type of cybersecurity that’s important to your organization.
I need a silver bullet solution!
Unfortunately, there isn’t one. Just like getting every single tool isn’t the solution, getting just one miracle tool isn’t the answer, either.
You need to get the basics in order—particularly, visibility and
training.
- Visibility. You need insight into what should and should not be on your network. Turn on applications that should be enabled and turn off those that shouldn’t.
- Training. Provide your organization with staff regular cybersecurity awareness training so you can be equipped with the knowledge you need to spot, respond to, and avoid cyber threats in the future.
But I’m not a target!
We wish that were true. However, every organization can be a target…especially when they deal with critical infrastructure.
Think you’re too big to get infiltrated? Cybercriminals have been able to hack government systems, multinational corporations, and tech giants. No target is too big.
Think you’re too small to be a target? Cybercriminals are known to launch attacks on smaller organizations as testing grounds or stepping stones for much larger attacks. No target is too small.
Healthcare practices like yours are
especially attractive targets because the data you handle can be worth a lot of money on the dark web, and cybercriminals will go to great lengths just to steal them.
There’s too much to do, I’ll never get anything done!
There is quite a lot to do when it comes to keeping critical infrastructures secure, but you don’t have to do all of them at the same time. You need to wrap your head around what’s important for your organization in particular.
In Ford’s words, one has to “separate the noise from the signal.” Find a way to know what your “crown jewels” are. Ask yourself this:
What critical services, endpoints, or technologies within your network architecture that, if they go down, will cause a cascading impact on your practice, patients, and partners?
These are the things you can start focusing on.
But we don’t own the risk!
Actually, you do. You may pay a person or a company to manage and monitor certain services, but at the end of the day, you ultimately still own the risk.
The US government will save us!
Unfortunately, the US government cannot save everybody when it comes to cybersecurity attacks on critical infrastructure.
This is why the partnership between the federal government and the private sector is key in minimizing cyber incidents in the future.
Partner up with healthcare IT experts!
Sorting through misconceptions is one thing, but implementing visibility, training, assessments, and cybersecurity strategies is quite another.
For the latter, you’re going to need to partner up with
tech experts who specialize in healthcare IT.
Know what’s going on with your network infrastructure, what cybersecurity solutions are available to you, and what you can do to fortify your defenses.
Protect the critical infrastructures you have in your organization by working with experts in healthcare IT, cloud, and compliance.
Search Articles
Healthcare & Tech Articles

ER Tech Pros is a managed service provider (MSP) that specializes in catering to the IT needs of businesses across the globe. We have offices in Sacramento and the Greater Fresno area.
We use our cutting-edge technology, extensive experience, and global team of technology experts to ensure your IT network is in its most secure and optimal state.
We focus on your IT so you can focus on growing your company.
8795 Folsom Blvd, Ste 205
Sacramento, CA 95826
1501 Howard Rd, Ste 2
Madera, CA 93637
(855) ER-TECH-1 / (855) 378-3241
info@ertech.io
Resources
Search this Site
ERTech Pros | All Rights Reserved.