What Is a Data Breach and How to Prevent It in Healthcare?
Healthcare data breaches continue to rise, putting patient trust and sensitive information at risk. This blog explains what a data breach is, why healthcare is a prime target, and how proactive data breach prevention strategies help protect systems, data, and patient confidence.

Healthcare organizations are right at the center of trust, technology, and sensitive data. Every appointment, claim, prescription, and diagnosis generates details that need to be guarded. Yet, despite our industry leaders’ best efforts, data breaches and cybersecurity incidents continue to rise and spread across healthcare spaces.
For many healthcare providers, cybersecurity becomes a top priority only after a serious incident occurs. That’s when organizations reach out to specialized healthcare cybersecurity partners, like ER Tech Pros, to seek help — not just to fix the problem, but to make sure it never happens again.
In fact, did you know that in 2024, the protected health information (PHI) of more than 276 million individuals was exposed or stolen in data breaches?
These alarming numbers highlight the fact that healthcare remains the most vulnerable industry for cyber threats, and preventive measures are the only solution to mitigate the effects.
This blog examines and informs what a data breach really means, why healthcare is targeted, and how proactive data breach prevention strategies can protect patients and workflows.
What Is a Data Breach?
A data breach takes place when sensitive, protected, or confidential information is accessed, revealed, or stolen without authorization. In the healthcare industry, this usually involves PHI, financial data, or credentials integrated with administrative platforms.
Unlike regular cybersecurity incidents, which are discovered and contained in the initial stages, a confirmed breach means that the data has already leaked through the security controls. This difference matters because it triggers breach notifications, regulatory reporting, financial penalties, and long-term efforts for data recovery.
Healthcare cybersecurity data breaches are extremely damaging because PHI cannot be changed the way a normal password can. Once leaked, patient data may circulate indefinitely, increasing long-term cybersecurity risks for both the organizations and people.
Types of Data Breaches in Healthcare
Data breaches in healthcare don’t usually follow the same pattern. Some unfold rapidly, while a few remain hidden for months before the affected organization discovers them.
Knowing these variations helps organizations build resilient data leak prevention and response strategies.
External Cyber Attacks
This mainly involves hackers exploiting vulnerabilities through malware, ransomware attacks, or stolen credentials. Once hackers gain access, they move laterally across the systems to gather as much information as possible.
These attacks account for many large-scale cybersecurity breaches. This is why experts from ER Tech Pros frequently help healthcare organizations identify how attackers entered and how far they’ve spread within the environment.
Internal Data Leaks
Not all healthcare data leaks are malicious. Staff may accidentally email or share sensitive files, change the access permissions, or store information in an unsecured space.
Even though unintentional, these accidents still qualify as breaches and highlight the need for data leakage protection strategies and regular training for employees.
Third-Party and Vendor Breaches
Many healthcare organizations rely heavily on vendors for billing, cloud hosting, and analytics. If a vendor suffers a data breach, patient details may be indirectly revealed.
ER Tech Pros stands out by assisting healthcare clients with risk assessments to mitigate these vendor-related cybersecurity risks.
Why Data Breaches Happen in Healthcare
Healthcare industries are advanced, fast-paced, and interconnected. This sophisticated environment increases both the attack surface and the chances of human errors.
Several factors lead to healthcare cybersecurity data breaches:
Usage of Traditional Systems
Several organizations still count on outdated systems that lack modern security controls. These systems are attractive targets for attackers scanning for known weaknesses.
Legacy systems continue to cause cybersecurity breaches, especially when updates are delayed.
Human Errors and Social Engineering
Cybercriminals leverage phishing emails, fake login pages, and phone scams to exploit staff members of healthcare organizations. Just one click on any of these can leak credentials or install malware.
Since humans interact with healthcare IT systems every day, staff members remain one of the biggest reasons why cyber threats happen.
Weak Network Security Controls
Poor segmentation, inconsistent access controls, and limited monitoring weaken the network security. Without visibility, suspicious activity can go unnoticed for long periods.
ER Tech Pros identifies these gaps during healthcare security assessments, helping organizations close blind spots before attackers exploit them.
How Does a Data Breach Happen?
Although data breaches vary, most follow a pattern that hackers typically use.
Understanding these patterns helps organizations strengthen their data breach prevention efforts.
Stolen Credentials
Credentials stolen through phishing or reused passwords allow attackers to log in undetected. Once inside, they often appear as legitimate users.
This makes password theft one of the most dangerous cyber threats that the healthcare industry faces on a daily basis.
Malware and Ransomware Attacks
Malware enters your system through emails, compromised websites, or unsecured devices. Ransomware attacks often escalate into cybersecurity data breaches when data is stolen before encryption.
Most of these attacks can disrupt care delivery and even force difficult operational decisions.
Exploited Vulnerabilities
Unpatched software, misconfigured servers, and exposed ports create easy entry points. Many cybersecurity incidents begin with vulnerabilities that were already known but not addressed.
This is why routine patching plays a major role in preventing data breaches.
What Information Gets Stolen in a Data Breach?
Healthcare breaches uncover details that can cause long-term damage for both individuals and organizations. The type of data exposed determines the severity of the impact.
Protected Health Information (PHI)
Medical histories, prescriptions, and lab results are usually exposed. PHI cannot be changed, making it extremely valuable to attackers.
This permanence of information increases the long-term harm caused by data breaches.
Personal and Financial Details
Names, addresses, Social Security numbers, and insurance details are frequently targeted. This data enables fraud and identity theft, extending the impact of cybersecurity data breaches well beyond healthcare systems.
Login Credentials and Access Tokens
Credentials allow attackers to return later or sell access to others. Without dark web monitoring, organizations may not know credentials have been exposed until damage occurs.
ER Tech Pros uses 24/7 dark web monitoring to identify leaked credentials early.
What Can Attackers Do with Stolen Data?
Once they successfully steal the data, attackers have multiple ways to profit or escalate harm. The damage often continues long even after the initial breach.
Sell Data on the Dark Web: Healthcare data commands high prices on underground markets. This demand keeps healthcare at the top of cybersecurity statistics year after year.
Commit Fraud and Identity Theft: Stolen information can be used to submit fake insurance claims, gain prescriptions, or unlock financial accounts.
Beyond the healthcare industry, these outcomes amplify the consequences of data breaches on patients.
Launch Follow-Up Attacks: Hackers may use stolen information to target connected systems or partner organizations, increasing overall cybersecurity risks across the healthcare ecosystem.
How to Prevent a Data Breach in Healthcare
Preventing data breaches requires multi-layered defenses that evolve as threats advance. Strong data breach prevention combines the right technology, processes, and people!
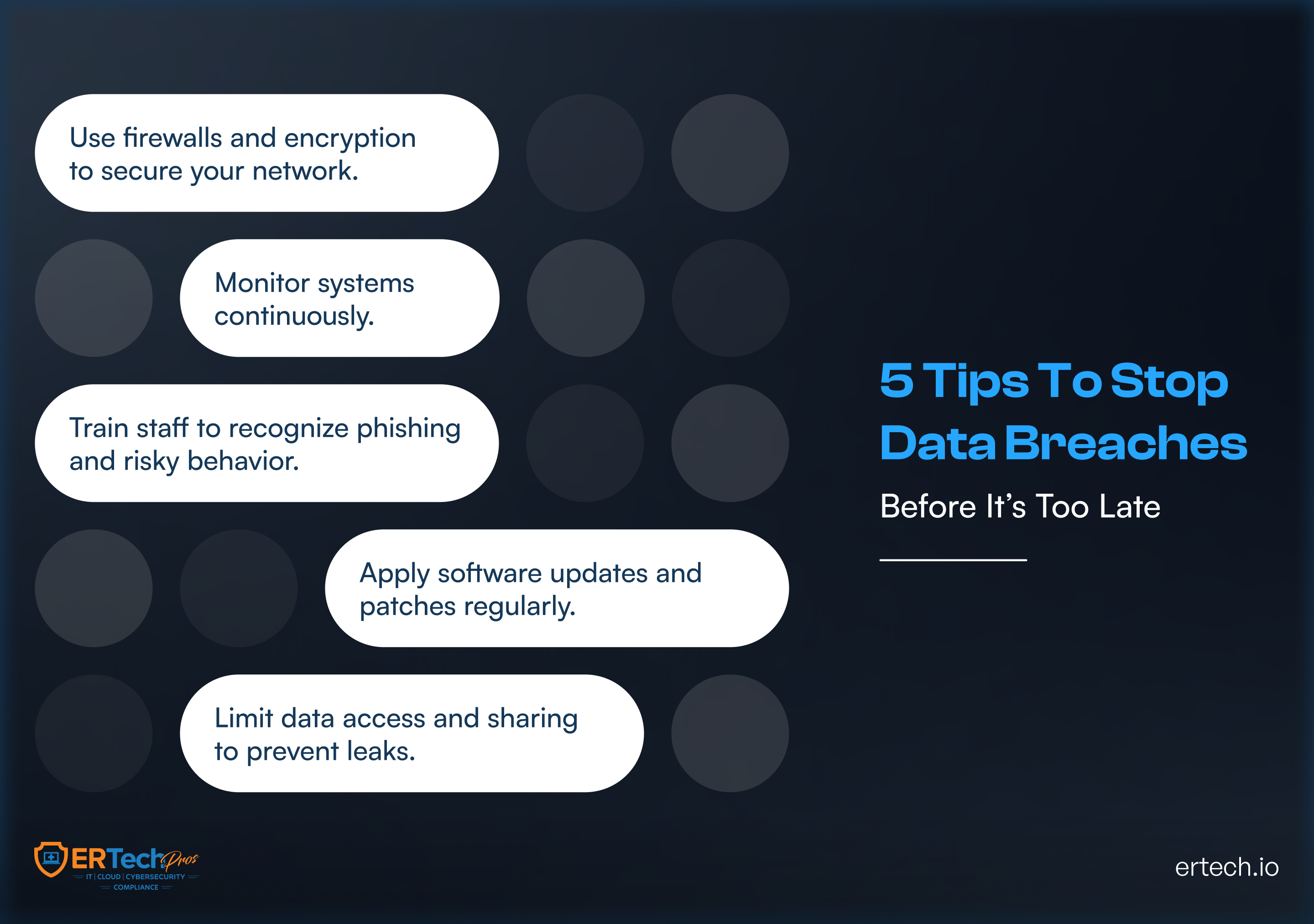
Strengthening Network Security
Firewalls, segmentation, encryption, and intrusion identification limit hacker movement and exposure.
Robust network security makes it difficult to execute breaches and easier to detect.
Continuous Monitoring and Detection
Real-time monitoring helps spot unusual activity early. Dark web monitoring adds another layer by alerting teams when passwords or data appear for sale.
ER Tech Pros integrates monitoring strategies customized to healthcare organizations and compliance standards.
Staff Training and Security Awareness
Regular training helps staff members recognize phishing attempts and risky behavior. And reducing human error significantly lowers the cybersecurity risk.
Regular Updates and Patch Management
Consistent updates terminate familiar vulnerabilities before hackers can use them. Additionally, automation ensures that no step is skipped.
Data Leakage Protection Controls
Restricting access and information sharing significantly lowers accidental exposure. Impenetrable data protection strategies help contain damage before mistakes happen.
Building Resilience Against Data Breaches
Healthcare data breaches are rapidly increasing, and the need for proactive data breach prevention has never been clearer.
Healthcare organizations that invest in network security, continuous monitoring, and healthcare-focused expertise are better equipped to protect patient trust. ER Tech Pros helps organizations move beyond reactive fixes and helps build cybersecurity strategies that align well with real clinical environments.
Protecting healthcare information is all about safeguarding care, continuity, and confidence.
Got Questions? We've Got Answers
Find clear answers to common questions that help guide your healthcare IT operations.
Healthcare IT Solutions Built for Every Critical Second

Key Reasons IT Disaster Recovery Should Be A Top Priority for Healthcare Organizations

Call Routing in Healthcare: Why It Matters and How to Do It Right?
